I. Introduction
A. The Increasing Threat of Instagram Hacking
In the age of digital connectivity, social media platforms like Instagram play a significant role in our lives. Unfortunately, with the increasing popularity of these platforms, the threat of hacking has also grown. This article aims to guide individuals on the steps to recover a hacked Instagram account, emphasizing the importance of swift action in such situations.
B. Importance of Swift Action
Recognizing the signs of a hacked account and taking immediate action is crucial to minimize potential damage. Delayed response may lead to unauthorized access, misuse of personal information, or even permanent loss of the account. This guide provides a comprehensive approach to recovering a hacked Instagram account.
II. Recognizing the Signs of a Hacked Instagram Account
A. Unusual Account Activity
Be vigilant for any unusual activities on your Instagram account, such as unfamiliar posts, comments, or interactions. Any unexpected changes in your account’s behavior may indicate unauthorized access.
B. Password Changes Without Authorization
If you receive notifications about password changes that you did not initiate, it is a clear sign that your account may be compromised. Instagram will send such alerts to your registered email or phone number.
C. Unexpected Email or Phone Number Changes
Check for any changes to the email address or phone number linked to your Instagram account. If these details are altered without your knowledge, it may indicate a security breach.
D. Unauthorized Posts and Messages
Keep an eye on your account’s content. If you notice posts or messages that you didn’t create, it’s a red flag. Hacked accounts often exhibit suspicious activities in the form of unauthorized posts or messages.
III. Immediate Actions to Take
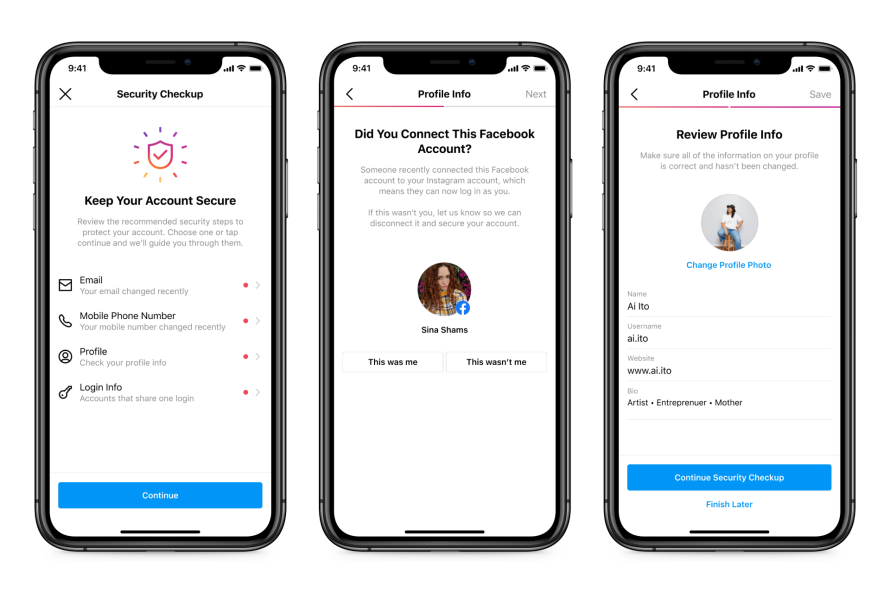
A. Change Your Password
The first step after suspecting a hack is to change your password immediately. Choose a strong and unique password that combines letters, numbers, and symbols.
B. Enable Two-Factor Authentication (2FA)
Enhance your account’s security by enabling Two-Factor Authentication. This adds an extra layer of protection by requiring a verification code in addition to your password for logins.
C. Log Out of All Devices
Instagram provides an option to log out of all devices currently using your account. This is crucial to ensure that the hacker loses access to your account.
D. Report the Incident to Instagram
Inform Instagram about the security breach by reporting the incident through the app or website. This initiates the official account recovery process.
IV. Initiating the Account Recovery Process

A. Using the Instagram App
Open the Instagram app and go to the login page.
Click on “Forgot Password?”.
Enter the email address or phone number associated with your account.
Follow the prompts to reset your password.
B. Via the Instagram Website
Visit the Instagram website and click on “Forgot Password?” on the login page.
Enter your email address or phone number.
Follow the instructions sent to your email or phone to reset your password.
V. Providing Required Information for Account Verification

A. Personal Details
During the recovery process, Instagram may ask for personal details to verify your identity. Be prepared to provide accurate information, such as your full name and the account creation date.
B. Previous Passwords
Remember and provide details about any previous passwords associated with your account. This information helps Instagram confirm your ownership of the account.
C. Associated Email or Phone Number
Confirm the email address or phone number linked to your Instagram account. This step is crucial for receiving account recovery instructions and notifications.
D. Recent Activities on the Account
Describe any recent activities on your account, such as posts, comments, or interactions. This helps Instagram support assess the authenticity of the recovery request.
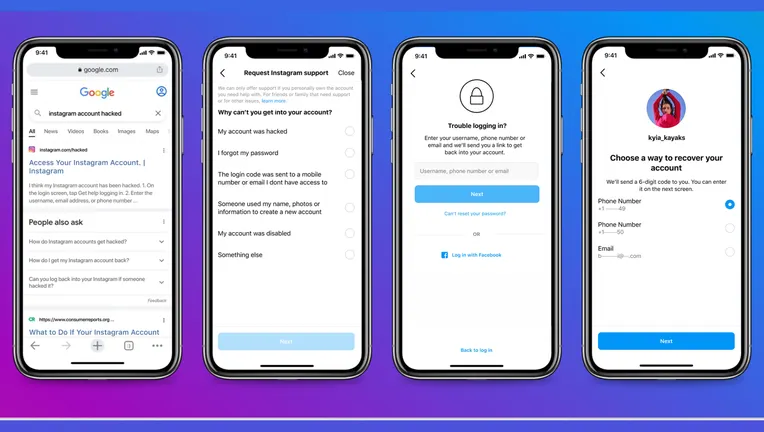
VI. Contacting Instagram Support

A. Submitting a Support Request
If the standard recovery process does not resolve the issue, submit a support request to Instagram. Provide detailed information about the hack, including the steps you’ve taken to recover the account.
B. Explaining the Situation Clearly
When contacting Instagram support, clearly explain the situation. Include relevant details, such as the date and time of the hack, any suspicious activities, and the steps you’ve taken to secure your account.
C. Following Up on the Request
Check the status of your support request regularly. If there’s no response within a reasonable time frame, consider submitting additional requests or reaching out through alternative channels.
VII. Additional Security Measures

A. Regularly Update Your Password
Prevent future hacks by regularly updating your password. Choose strong and unique combinations, and avoid using the same password across multiple platforms.
B. Monitor Third-Party Apps and Permissions
Review and manage third-party apps linked to your Instagram account. Remove any unnecessary apps and review the permissions granted to ensure optimal security.
C. Be Wary of Phishing Attempts
Stay vigilant against phishing attempts. Avoid clicking on suspicious links or providing login credentials on unofficial websites. Verify the authenticity of emails or messages claiming to be from Instagram.
VIII. Learning from the Experience
A. Strengthening Your Account Security
Use the hacking incident as an opportunity to enhance your account security. Implement additional measures such as stronger passwords, regular security checks, and awareness of potential threats.
B. Educating Others About Hacking Risks
Share your experience with friends and followers to raise awareness about the risks of hacking. Encourage others to prioritize security measures and remain vigilant against potential threats.
IX. Conclusion
Recovering a hacked Instagram account requires a combination of immediate actions, careful verification, and persistence in seeking support. By following the steps outlined in this comprehensive guide, users can enhance their chances of regaining control over their accounts and minimize the impact of a security breach. Stay proactive, stay secure, and contribute to a safer online community.

